Have you ever wondered what a proxy server is and how it works? Think of it as a middleman between your computer and the internet.
In this article, I’ll talk about how proxy servers keep your online browsing private and why they’re useful. It’s simpler than you might think, and I’ll explain it in an easy-to-understand way. Let’s get started!
What is a Proxy Server?
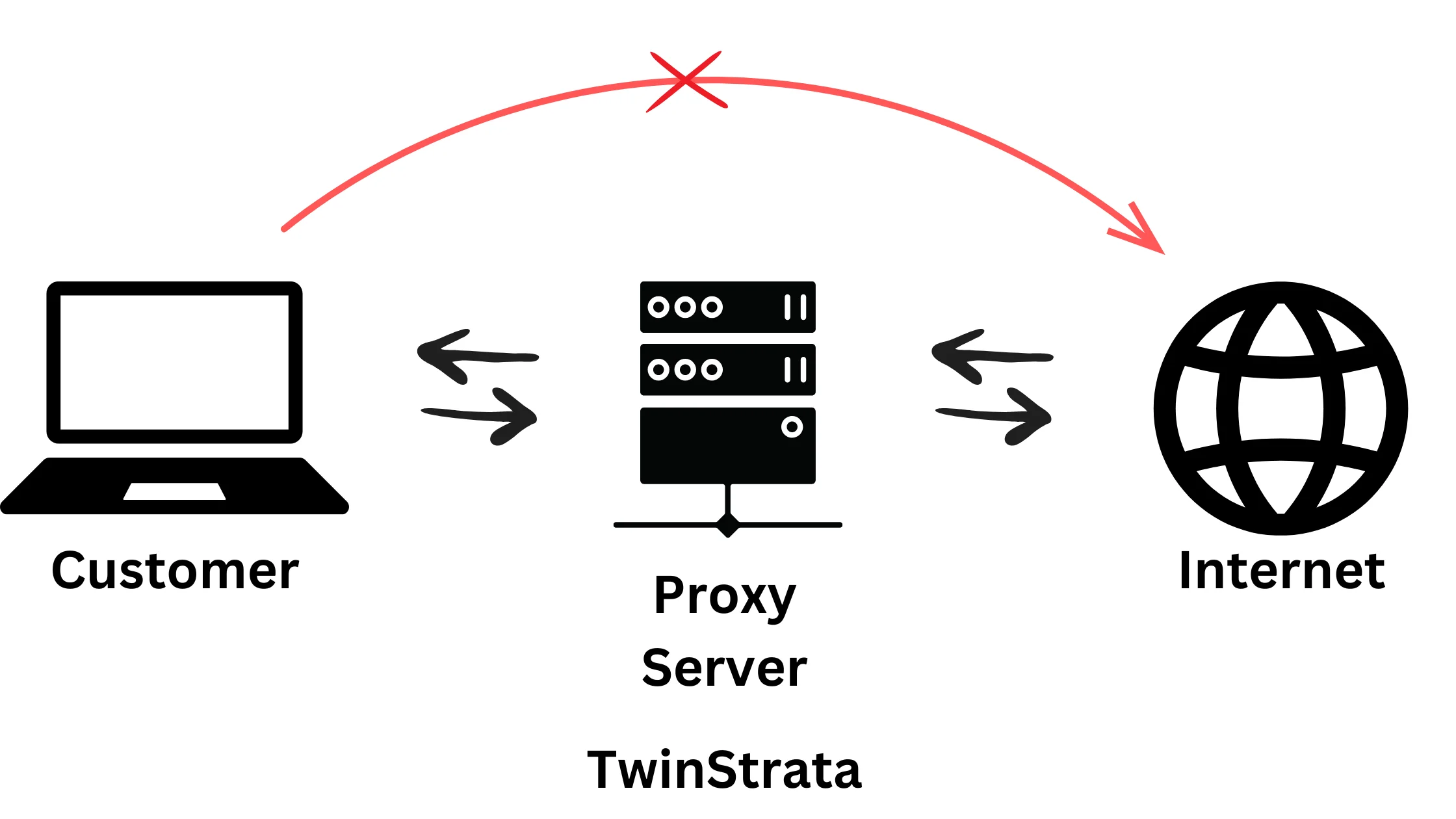
Proxy servers act as intermediaries between your computer and the internet. It separates users from the websites they access.
When you use a proxy server, your internet request is routed through this server to the website you want to visit. The response from the website also goes back through the proxy server before reaching you.
Proxy servers are not just for passing information back and forth. They have several important functions related to security and network performance.
These servers can act as a firewall and web filter, enhancing your internet security. They also provide shared proxies network connections, which can improve network efficiency.
Another key function is caching web data, which helps in speeding up access to frequently visited websites.
One of the major benefits of using a proxy server is the level of privacy it offers.
By routing your requests through a proxy, your direct interaction with websites is masked, providing an additional layer of anonymity on the internet. This makes proxy servers a valuable tool for both individual privacy and corporate security.
How Does a Proxy Server Operate?
On the Internet, each computer has its own unique Internet Protocol (IP) Address, which is essential for identifying the computer’s location on the Web, similar to a street address in the physical world.
This IP address allows the internet to direct the correct data to the right computer, much like how the postal service delivers mail to your home.
A proxy server is another computer on the internet that has its own IP address, which your computer recognizes.
When you use a proxy server and send out a web request, like trying to visit a website, your request is sent to the proxy server first.
The proxy server then sends out the request on your behalf, receives the response from the website, and finally sends the web page data back to you. This process allows you to view the website in your browser.
The proxy server does more than pass information back and forth. It can modify the data you send. For instance, it can change your IP address.
This means the website you’re visiting doesn’t see your actual location, adding a layer of anonymity. The proxy server can also encrypt your data, making it secure and unreadable as it travels through the internet.
Additionally, it can block access to certain web pages based on their IP addresses, which adds a level of control over the content accessible through your network.
Why Should You Use a Proxy Server?
1. Controlling Internet Usage
Organizations and Parents: Both companies and parents use proxy servers to oversee internet usage. For organizations, this means ensuring employees don’t visit inappropriate websites during work hours. They configure the proxy server to block access to certain sites, maintaining a professional work environment. Parents can similarly monitor and restrict their children’s internet access.
Monitoring Web Requests: Proxy servers log web requests. This means that even if a site isn’t blocked, organizations can track how much time employees spend on non-work-related browsing. For example, if an employee spends too much time on social media, the proxy log will show this.
2. Bandwidth Savings and Improved Speeds
Network Performance: Proxy servers enhance network efficiency by caching popular websites. For instance, if multiple employees visit the same site, the proxy server stores and provides a local copy, reducing the load on the company’s internet bandwidth.
Suppose in a school, lots of students and teachers regularly check the weather on a site like www.weather.com. Without a proxy, each person’s computer would send a separate request out to the weather site, using up a lot of the school’s internet bandwidth.
But with a proxy server, the first time someone checks the weather, the proxy server keeps a copy of that page.
Then, when the next person wants to see the weather, the proxy server shows them the copy it saved. This means fewer requests go out to the actual weather website, saving the school’s internet bandwidth and making the page load faster for everyone.
3. Privacy Benefits
Masking IP Addresses: Proxy servers can change the IP address in a web request, making it difficult for the destination server to determine the true origin of the request. This is beneficial for individuals who want to keep their location and browsing habits private.
For instance, if you’re in New York and don’t want a website to know your real location, the proxy can make it appear as if you’re accessing the internet from a different city or even a different country.
4. Improved Security
Encryption and Malware Protection: Proxy servers can encrypt web requests, making the data unreadable to outsiders. They can also block access to known malware-infested sites, protecting the network.
Integration with VPN: For remote employees, organizations can combine proxy servers with VPNs. This ensures that remote access is secure and that employees can safely access internal resources.
Example of Improved Security: When an employee working from home accesses the company network, the VPN-Proxy combination ensures that their connection is not only secure from eavesdroppers but also that they have safe access to internal company resources.
5. Access to Blocked Resources
Circumventing Content Restrictions: Proxy servers are like digital gateways that can help you get around certain online restrictions based on your location.
Imagine you’re in India, and there’s a special TV show that you can only watch in the United Kingdom. Normally, if you try to watch it from India, you won’t be able to because of location-based restrictions.
But, if you use a proxy server that’s located in the UK, it’s like you’re accessing the internet as if you were in the UK. So you can watch the show without any issues.
6. Proxy Server Risks
Performance and Security Issues: Free proxy servers may not invest in robust hardware or encryption, leading to performance problems and data security risks. Since they are often ad-supported, they might not prioritize user privacy and security.
Example of Risk: A free proxy service might have slow connection speeds and could potentially be a target for data thieves. It’s like choosing a free but unreliable taxi service, where you risk your safety and timely arrival.
7. Browsing History Log
Data Storage Concerns: Proxy servers store your IP address and web requests, sometimes without encryption. It’s crucial to check their data logging practices and how they cooperate with law enforcement or third parties.
Privacy Implications: If a proxy server logs and sells your data, it defeats the purpose of using it for privacy. For example, a proxy service might track and sell your browsing history, negating any privacy benefits.
8. No Encryption
Vulnerability to Data Breaches: Using a proxy server without encryption is risky, as your data travels in plain text. This makes it easy for hackers to intercept sensitive information like usernames and passwords.
Importance of Encryption: Always ensure the proxy server offers full encryption. For example, if you’re transmitting credit card information or passwords, encryption is essential to protect this data from eavesdroppers.
Types of Proxies:
1. Forward Proxy Server
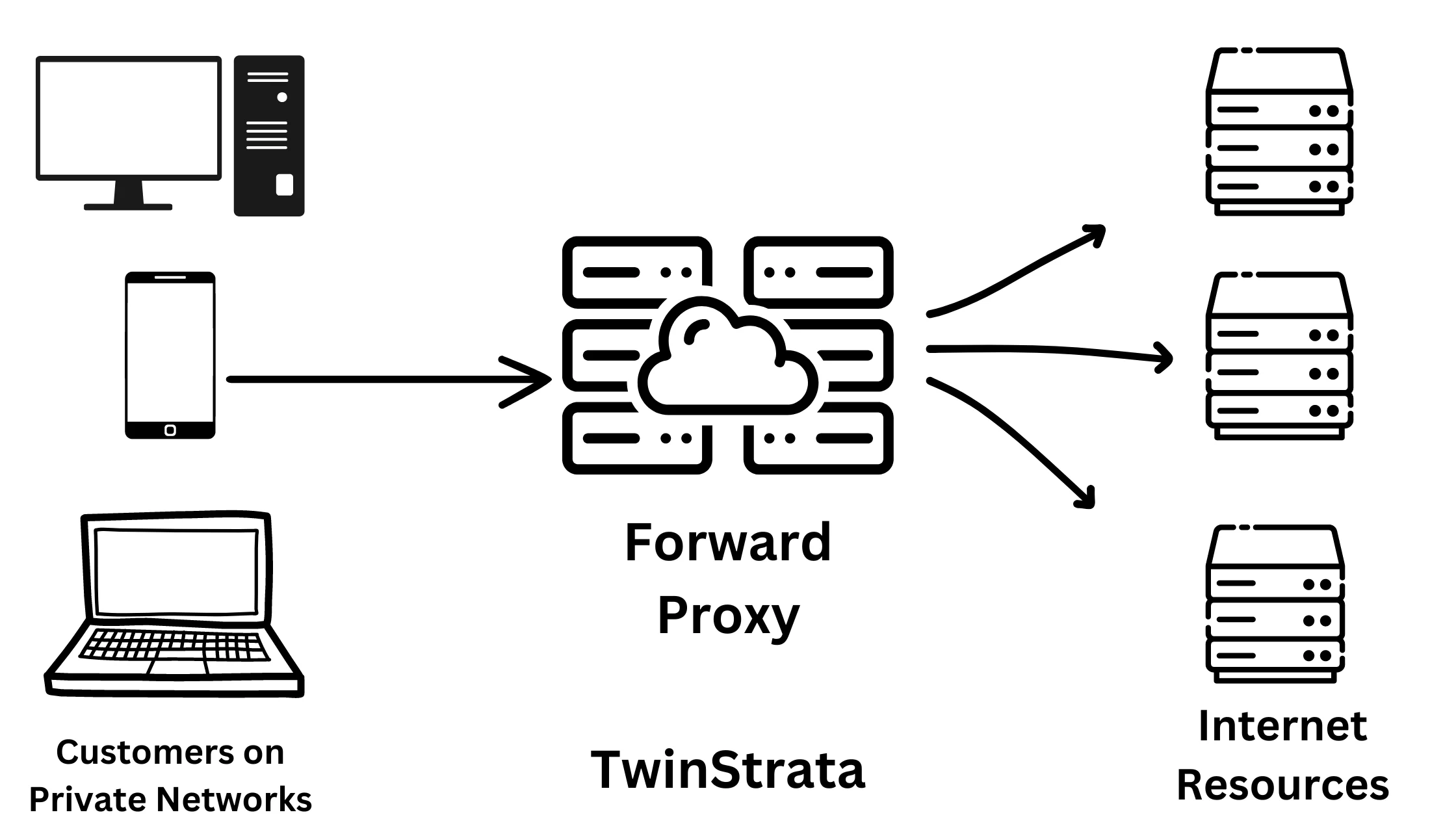
A Forward Proxy Server acts as the middleman between users on an internal network and the wider internet. Here’s how it works: when you make a request to visit a website, this request first goes to the forward proxy.
The proxy then evaluates this request, deciding whether to allow or deny it based on set rules. If allowed, it forwards your request to the internet through a firewall. When the web server responds, the forward proxy receives this response and then passes it back to you.
An interesting feature of forward proxies is their ability to store (or cache) frequently requested data. If the data you request is already cached, the proxy quickly retrieves it without fetching it anew from the internet. This not only speeds up access but also reduces bandwidth usage.
2. Reverse Proxy Server
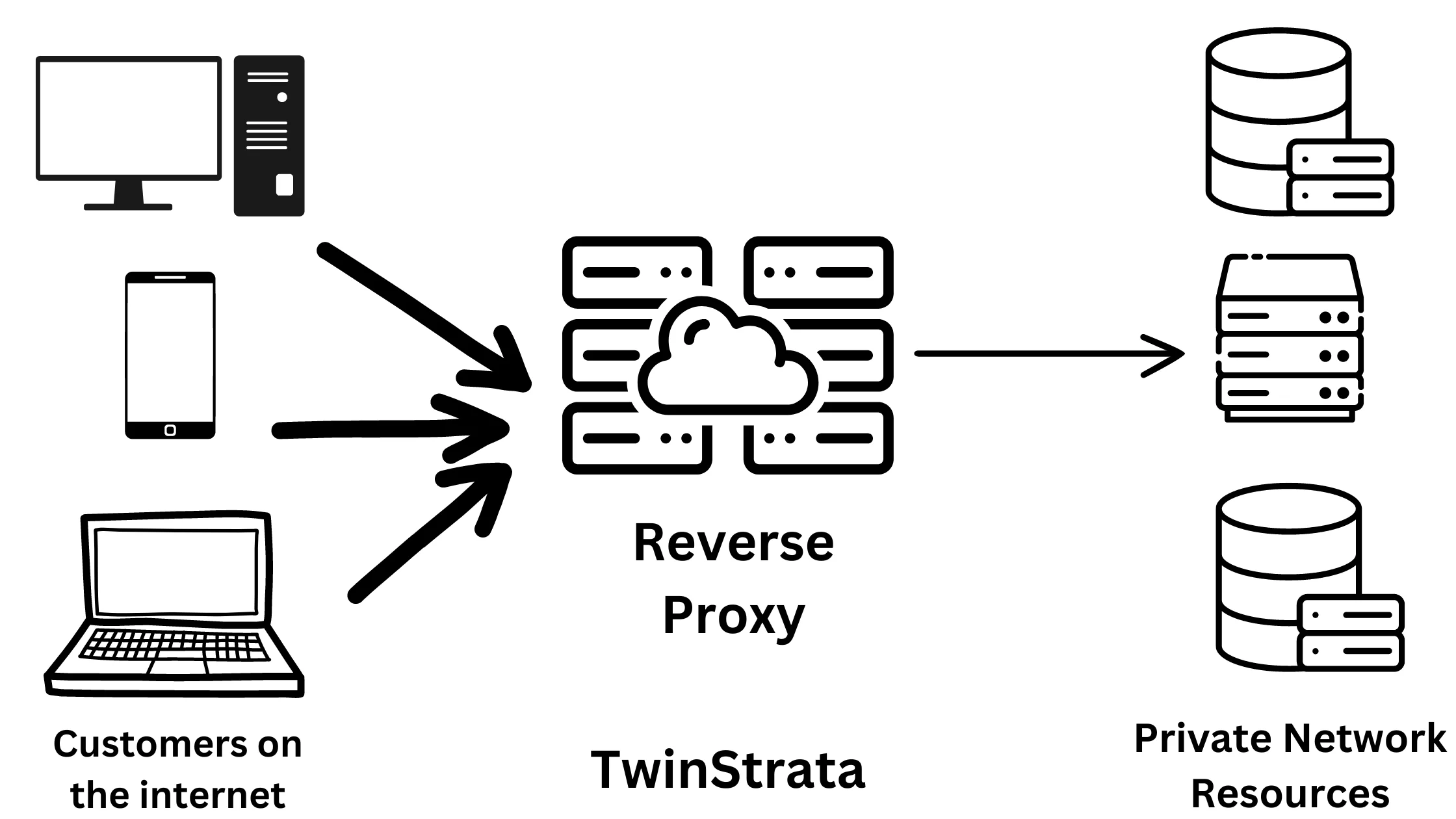
Think of a Reverse proxy server as the opposite of a Forward proxy server, acting as a mirror image. It primarily deals with incoming requests from the outside world to an internal network, usually passing through a firewall.
Reverse proxies are particularly useful in environments where control over access to sensitive data is crucial.
They act as a protective layer for backend servers, managing and directing incoming traffic. Like forward proxies, they, too, can cache data.
This means if the requested information is already available in the cache, the reverse proxy swiftly delivers it without bothering the backend servers, enhancing speed and efficiency.
3. Anonymous Proxy Servers
Anonymous Proxy Servers are all about privacy. They fall into different levels based on the degree of anonymity they provide:
- High Anonymity Proxy (Level 1): These are the top-tier proxy server privacy. They completely hide your IP address and don’t even reveal to websites that they are proxy servers. What makes them stand out is their ability to frequently change IP addresses, making it extremely difficult to trace any activity back to your original IP. This level of proxy is ideal for users who prioritize the highest degree of privacy and security in their online activities.
- Anonymous Proxy Server (Level 2): These proxies are a step down from high anonymity proxies, but they still offer significant privacy. They hide your real IP address from websites and present a different one, often in a different geographic location. This can be particularly useful for accessing content that’s restricted in your actual location or avoiding targeted ads. However, unlike high anonymity proxies, they do identify themselves as proxies to websites.
- Transparent Proxy Server (Level 3): At the other end of the spectrum, transparent proxies offer the least amount of privacy. They don’t hide your IP address or the fact that they’re proxy servers. Organizations, schools, and public libraries commonly use them for content filtering. Network administrators typically set them up and are not intended for users seeking privacy. Transparent proxies are easy to set up and maintain, making them a practical choice for controlling and monitoring internet usage in institutional settings.
Each type of anonymous proxy server serves a different purpose, ranging from maximum privacy protection to content management and monitoring.
Your choice of proxy server should align with your specific needs, whether it’s to maintain anonymity, bypass geo-restrictions, or manage internet usage within an organization.
Proxy Server V/s VPN
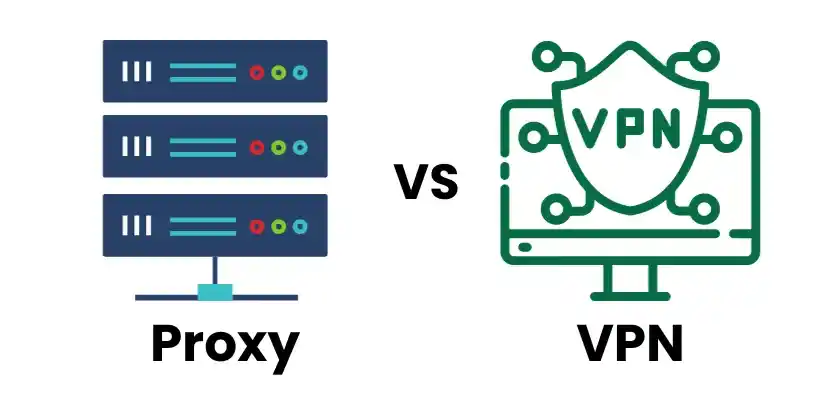
| Features | Proxy Server | VPN |
| Connection scope | Individual application or browser configuration | System-wide, all traffic flows through unless specifically excluded |
| Data encryption | Variable depends on the protocol (typically less secure than VPNs) | Yes, it creates an encrypted tunnel |
| IP address masking | Yes, changes the IP address associated with your traffic | Yes, it hides your true IP address |
| Security | Generally less secure, varies by protocol and configuration | Generally more secure due to encryption and system-wide coverage |
| Privacy | Offers some privacy by masking IP address, but may not encrypt data | High level of privacy by encrypting all traffic and hiding IP address |
| Speed | Typically faster than VPNs due to less processing overhead | It can be slower than proxies due to encryption and additional routing |
| Control | Requires individual configuration for each application | Automatic system-wide protection, with optional app exclusions |
| Typical use cases | Bypassing geo-restrictions, accessing blocked content, hiding IP addresses for specific applications | Enhancing overall online security and privacy, anonymizing all internet traffic |
Is it safe to use a proxy server?
Using a proxy server can be a useful tool for safeguarding your online privacy, but it’s essential to consider your specific needs and preferences to ensure safety. The type of proxy you choose matters; some may reveal your IP address, while others offer better anonymity.
Always check if a proxy logs your data and whether it’s encrypted to protect your online activity. Private proxies tend to be safer as they provide exclusive access. Be cautious with free proxies, as they might not offer strong security measures.
Ultimately, your choice should align with your privacy concerns, so take the time to research and select a proxy that suits your individual requirements. Your online safety and privacy are worth the extra effort.
How to set up a proxy server?
Setting up a proxy server can be done by configuring your device’s network settings, and the process can vary depending on your operating system or web browser. Here’s a general overview:
1. Find Proxy Settings: First, locate the proxy settings in your device or browser.
- On macOS: For Mac users, go to “System Preferences” and find the proxy configuration settings for Wi-Fi or Ethernet connections.
- On iOS: If you’re using an Apple iPhone, the proxy configuration settings can be found in your device’s Wi-Fi settings.
- On Windows 10: For Windows users, access proxy configuration settings through “Internet Options” > “Connections” > “LAN Settings.”
- On Safari: In the Safari web browser, proxy configuration settings can be found within the app’s System Preferences.
- On Mozilla Firefox: Firefox users should look for proxy configuration settings in Firefox’s Network Settings.
- On Google Chrome: Chrome users can access proxy configuration settings through “Devices” > “Networks.”
2. Configure Proxy: Once you’ve found the proxy settings, you’ll need to enter specific information:
- Proxy Server Address: This is the address of the proxy server you want to use.
- Port Number: Specify the port number associated with the proxy server.
- Additional Settings: Depending on your needs, you may need to enter other proxy-related information, such as authentication credentials or advanced settings.
3. Save Settings: After entering the necessary information, save your settings or apply the changes.
Keep in mind that the exact steps and locations of proxy settings can vary based on your specific device, operating system version, and web browser.
Therefore, it’s essential to refer to the provided links or consult the official documentation for your particular setup to ensure accurate configuration.
Setting up a proxy server can help protect your online privacy or access geo-restricted content. Still, it’s important to use this functionality responsibly and in accordance with any applicable laws and regulations.
Quick Links:
- How Proxies Help Improve Ad Verification?
- How to Test Proxies?
- Datacenter Proxies vs Residential Proxies
Conclusion
Now that I’ve discussed what a proxy server is and how it works feel free to ask any questions or seek further clarification if there’s anything you’d like to know more about or if you have any doubts. I’m here to help with any additional information you may need.
FAQs
What is a Proxy Server?
A proxy server acts as an intermediary server that sits between different networks or services, facilitating various functions such as data forwarding, filtering, and caching.
What is a proxy server used for?
Proxy servers serve multiple purposes, including enhancing functionality, bolstering security, and preserving privacy. They enable network administrators to manage and monitor employees' internet usage, optimize bandwidth for faster connections, balance loads between services, and access resources that might otherwise be blocked or restricted.
Is a VPN a proxy?
Virtual Private Networks (VPNs) can be considered a specific implementation of a proxy server. While both proxies and VPNs serve as intermediaries, VPNs extend their functionality by encrypting transmitted data, providing an additional layer of security and privacy. For a detailed comparison between proxies and VPNs, you can refer to our related post.
